Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development
Researcher: McAfee URL Security Service Gave Pass to Trojan
But ClickProtect Worked as Designed, McAfee Contends
A security researcher has noticed a snafu involving a McAfee security feature designed to scan and block malicious links sent via email.
See Also: Key Security Challenges and Tooling Approaches for APAC in 2024
A Paris-based researcher who goes by the nickname Benkow on Twitter noticed a potent type of banking malware known as Emotet appeared to be distributed through a URL that carries the same domain as McAfee's ClickProtect.
ClickProtect rewrites all URLs in an email message to ones that use the domain "cp.mcafee.com" instead. Once that conversion is done, the service analyzes the link to see if it's malicious and then scans it again every time someone else clicks it, according to McAfee's website.
Administrators can configure ClickProtect in a number of ways. If a user encounters a URL ranked as "medium risk," for example, administrators can choose to display a warning outlining the risk but giving users the option of continuing. Or certain URLs can be completely blocked, thus entirely eliminating any risk.
Benkow, however, found that a URL registered under McAfee's ClickProtect's domain still led to a malicious Microsoft Word document that carried Emotet. He's posted a link to an analysis of the malicious document.
After further digging, Benkow found that this doesn't appear to be a new snafu because a Salesforce.com administrator described witnessing a similar problem several years ago.
In a statement, however, McAfee says it has investigated Benkow's alert and found "the ClickProtect feature operated as designed." McAfee adds that "the concerns raised arose out of the timing of ClickProtect's reputation-based status detection and response."
Better Explanation?
Some observers contend that McAfee's explanation comes up short.
Picking up on Benkow's research, Jerome Segura, lead malware intelligence analyst with security firm Malwarebytes, analyzed the traffic flow for the suspicious ClickProtect URL. Once clicked, it redirects from McAfee's ClickProtect domain to another domain before finally ending up on a URL for the malicious Microsoft Word document.
A screenshot of the traffic flow shows a heading that says "blocked request," suggesting that McAfee's ClickProtect intended to block any errant click on the malicious link. Nevertheless, the link was still able to redirect the user to the malicious URL.
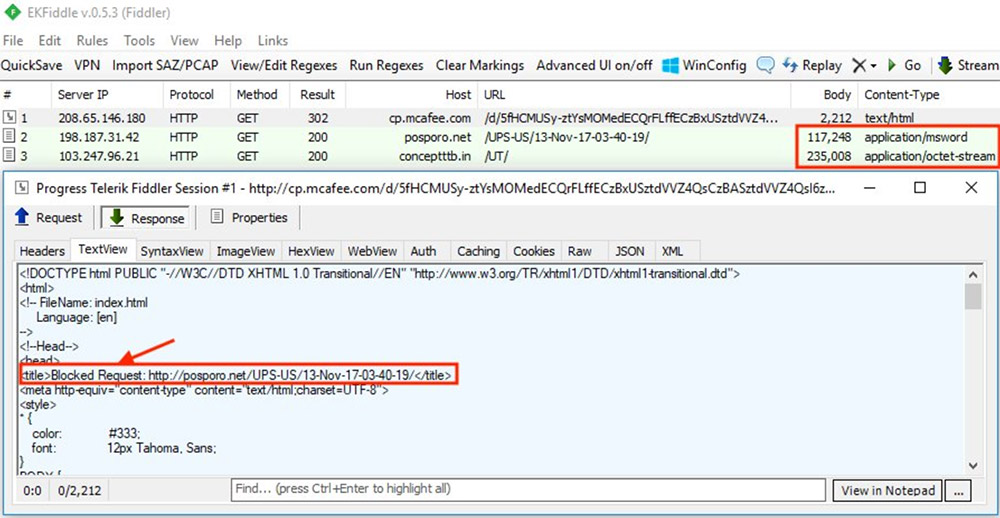
"Shouldn't it be blocking the redirection though?" Segura tweeted.
"Yep the system seems broken," Benkow replied.
From Low to High Risk
Another security researcher who goes by "James in the Box" entered the suspicious URL into a McAfee service that checks the reputation of a link and categorizes the potential danger it appears to pose. At least at the time, the URL in question was described as posing "minimal risk."
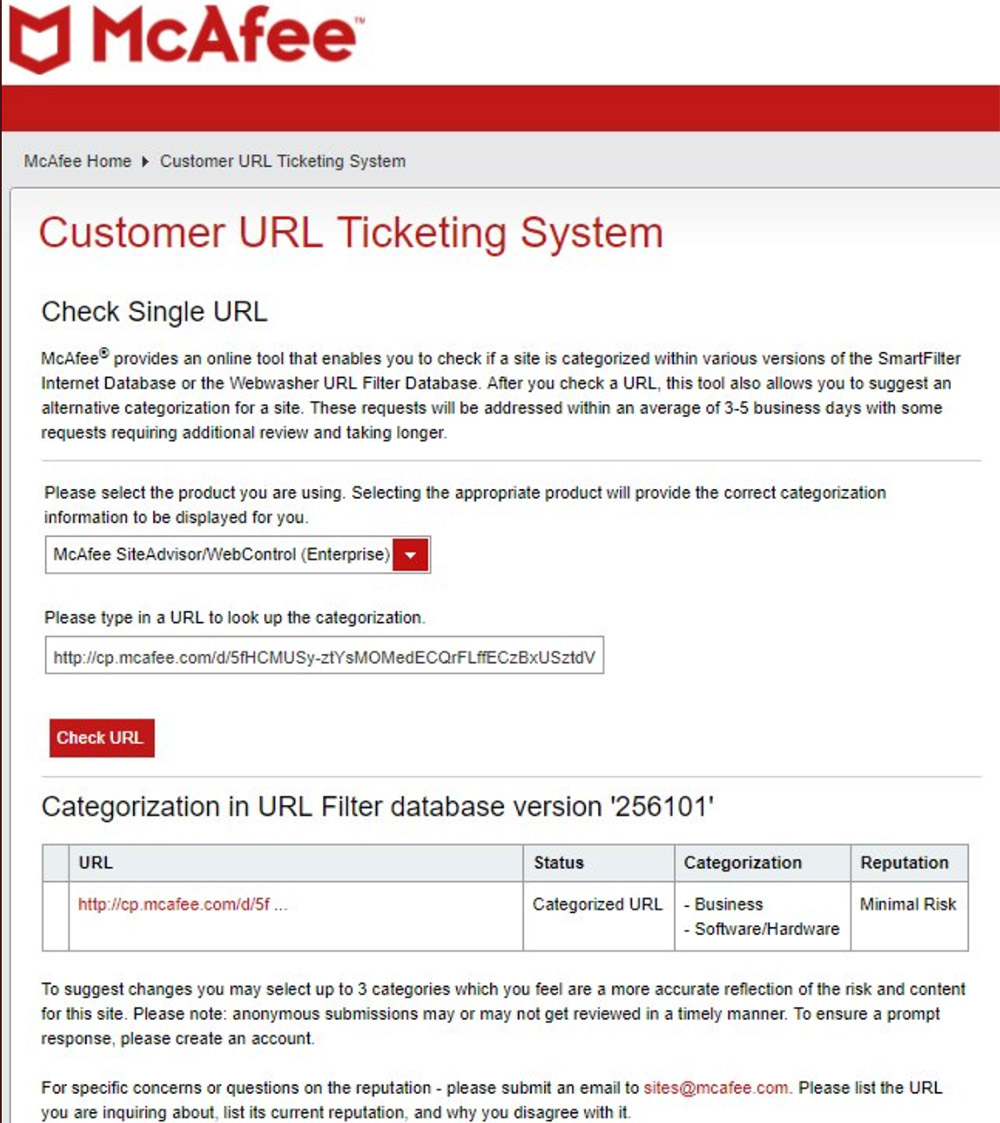
McAfee says that designation eventually changed, but it's not clear how quickly. In theory, McAfee's service should be doing this very fast because it's intended to stop people from browsing to malicious sites that infect their systems, simply because they clicked the wrong link.
McAfee confirms that its link-rating service now classifies the URL as a threat. "As soon as McAfee's Global Threat Intelligence service identified the web property as a threat, it changed the site's reputation ranking from 'low risk' to 'high risk,' and thereafter blocked McAfee customers from being able to reach the site," the company says in a statement. Again, however, it's not clear how quickly this happened.
Deja Vu
The incident parallels another from several years ago, in which an administrator posted to Salesforce.com's user forums a warning that a spam URL was registered under McAfee's ClickProtect domain.
"One of our clients logged a case with us today stating that they received an email seemingly from their Salesforce org," Kyle Dugger, a Salesforce certified administrator based in Tennessee, wrote in his post. "A small bit of research yielded the conclusion that the email is a spam Trojan virus email that contains an installer link."





















